Google, Dutch partner crack SHA-1
Q. SHA-1 is a cryptographic technology which stands for _________- Published on 24 Feb 17a. Secure Hash Algorithm-1
b. Social Hash Algorithm-1
c. Simple Hash Algorithm-1
d. Superior Hash Algorithm-1
ANSWER: Secure Hash Algorithm-1
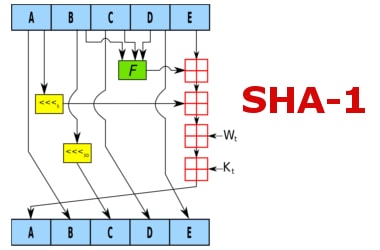
A collaboration between Google's research unit and a Dutch institute on Thursday cracked a widely used cryptographic technology SHA-1.
This technology that has been one of the key building blocks of internet security, is known as Secure Hash Algorithm 1 or currently used to verify the integrity of digital files and signatures that secure credit card transactions as well as Git open-source software repositories.
Researchers were able to demonstrate a "collision attack" using two different PDF files with the same SHA-1 fingerprint, but with different visible content.
Moving forward, it's more urgent than ever for security practitioners to migrate to safer cryptographic hashes such as SHA-256 and SHA-3.
SHA-1: Know More- In cryptography, SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function.
- It is designed by the United States National Security Agency.
- It is a U.S. Federal Information Processing Standard published by the United States NIST.
- SHA-1 produces a 160-bit (20-byte) hash value known as a message digest.