|
Describe Domain Name System.There are two types of client/server programs.
First is used directly by the user, such as e-mail, Second supports other application programs. The Domain Name System (DNS) is a supporting program that is used by other programs such as to find the IP address of an e-mail recipient.
|
|
Describe Hierarchical Namespace.In a hierarchical name space, each name is combination of several parts as: Type of the organization. Name of an organization. Departments in the organization. A central authority can assign the part of the name that defines the nature and name of the organization. The other things of the name the organization provides itself. The organization can add suffixes (or prefixes) to the name to define its host. The company need not worry about the prefix if it is same as that of another organization because, even if part of an address is the same, the whole address is different. Example:Suppose central authority has given names ABC.com and XYZ.com to two separate organization but these organization can add prefix as career so the name becomes career.XYZ.com and career.ABC.com. The names are unique without the need for assignment by a central authority. The central authority controls only part of the name, not the whole. 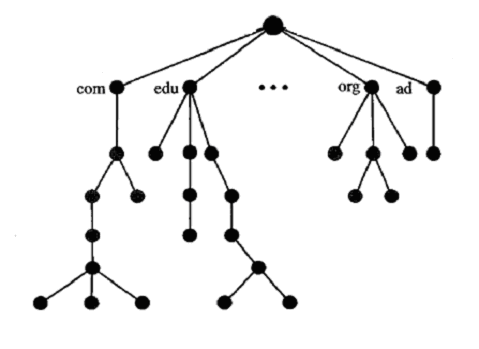
|
|
Define Fully Qualified Domain Name and Partially Qualified Domain Name.In hierarchical name space, names are defined in an inverted-tree structure with the root at the top. The tree can have only 128 levels: level 0 (root) to level 127. Each node in the tree has a label, which is a string with a maximum of 63 characters. The root label is a null string (empty string). In this tree, all the labels have different name, which guarantee the uniqueness of the domain names. A full domain name is a sequence of labels separated by dots (.). The domain names are always read from the node up to the root. Fully Qualified Domain NameIf a label is terminated by a null string or empty string, it is called a fully qualified domain name (FQDN). Partially Qualified Domain NameIf a label is not terminated by a null string, it is called a partially qualified domain name (PQDN). A PQDN starts from a node, but it does not end with the root. What is transmission impairment?Signals need transmission media for travel from one point to another. Transmission media are not perfect because it provides resistance. The imperfection causes signal impairment. This means that the signal at the beginning of the medium is not the same as the signal at the end of the medium. What is sent is not what is received. There are three causes of impairment are attenuation, distortion, and noise. 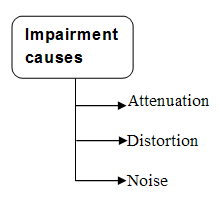
|
|
Describe attenuation, distortion, and noise in brief.Attenuation: When a signal travels through a medium, it loses some of its energy due to resistance of the medium. This loss of energy is called Attenuation. This is the reason why a wire carrying electric signals gets warm. Some of the electrical energy in the signal is converted to heat. To overcome for this problem, amplifiers are used to amplify the signal. Unit of the decibel is used to find out if a signal has lost or gained strength. The decibel (dB) measures the relative strengths of two signals or one signal at two different points. If decibel is negative then a signal is attenuated and if positive signal is amplified. Formula: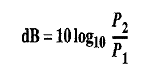 Where PI and P2 are the variable and the powers of a signal at points 1 and 2, respectively. DistortionWhen the signal travels through the medium from one point to another it may chance to change the form or shape of signal. It is called distortion. Distortion can occur in a composite signal, made up of different frequencies. Each signal component has its own propagation speed through a travelling medium and, therefore, its own delay in reaching at the final destination. Means signal components at the receiver have phases different from what they had at the sender. NoiseThe third cause of impairment is Noise. Following types of noise are possible. -Thermal noise.-Induced noise.-Crosstalk noise. -Impulse noise.These noise may corrupt the signal. Thermal noise is produced due to the random motion of electrons in a wire which creates an extra signal not originally sent by the transmitter. Induced noise comes from sources such as motors and other electronic appliances. These devices act as a sending antenna, and the transmission medium acts as the receiving antenna. Crosstalk is the effect of one wire on the other. Impulse noise comes from power lines, lightning etc.
|
|
Describe composite single.Composite Signals are the combination of more than one sine waves. Simple sine waves can be used to carry electric energy from one place to another or we can use a single sine wave to send an alarm to a security center when a thief opens a door or window in the house. A single frequency sine wave is not useful in data communications we need to send a composite signal. A composite signal can be periodic or non-periodic. The figure of composite periodic signal is given below. 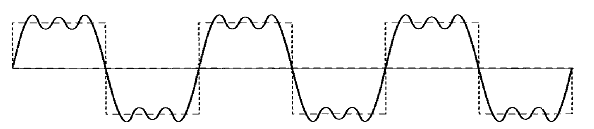
|
|
Describe MIMEElectronic mail has a simple structure. It can send messages only in NVT 7-bit ASCII format. It cannot be used for those languages that are not supported by 7-bit ASCII characters so languages such as French, German, Hebrew, Russian, Chinese etc cannot use this format. Also, it cannot be used to send binary files or video or audio data. We need a protocol that allows non-ASCII data to be sent through e-mail. So Multipurpose Internet Mail Extensions (MIME) is the answer. MIME transforms non-ASCII data at the sender site to NVT (Network Virtual Terminal) ASCII data and delivers them to the client MTA to be sent through the Internet. The message at the receiving side is transformed back to the original data. Main task of MIME is to transform non-ASCII data to ASCII data and vice versa. 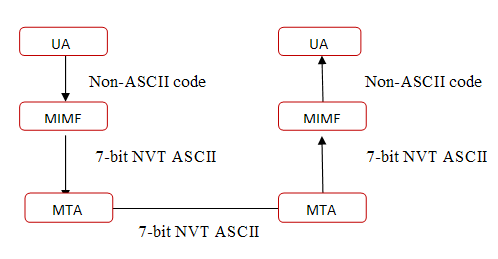 MIME header MIME headerMultipurpose Internet Mail Extensions defines five types of header. 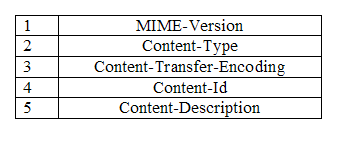
|
|
SMTP is push protocol Justify your answer.SMTP is a push protocol; it pushes the message from the client to the server. For sending email SMTP is used two times, between the sender and the sender's mail server and between the two mail servers. To send mail, a system must have the client MTA (Message transfer agents), and to receive mail, a system must have a server MTA. SMTP uses commands and responses to transfer messages between an MTA client and an MTA server. Commands are sent from the client to the server and Responses are sent from the server to the client. SMTP is not used in pulling the message. 
|
|
Describe the POP3 protocol.Post Office Protocol, version 3 is used for accessing the message. POP3 is very simple protocol and has limited functionality. POP has different version but currently version 3 is used. A POP3 server listens on well-known port 110. POP3 supports two types of mode.
Delete Mode: In this mode, the mail is deleted from the mailbox after each retrieval.
Keep Mode. The mail remains in the mailbox after retrieval.
|
|
Describe IMAP4 (Internet Mail Access Protocol) in detail.This protocol is also used in Internet for accessing the mail. IMAP4 has more feature than POP3 and is more powerful. Main difference in POP3 and IMAP4 are as follows. 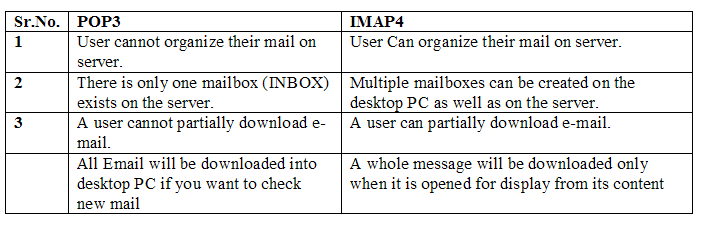
|
|
What is Anonymous FTP?Some sites provide the functionality that user can access the file with limited access. To access these files, a user does not need to have an account or password. For using FTP, the user enters "anonymous" as a user ID and guest as password. Usually, you can enter anything as a password.
|
|
What is User Agent?User agent is a software that provides the service to the user to make the process of sending and receiving a message easier. The following are User Agent services. 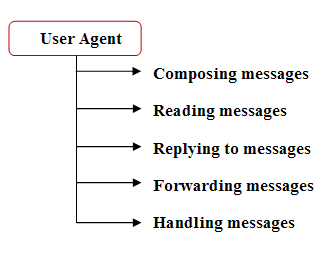
|
|
Describe Classful Addressing IPv4 addressing uses the concept of classes. In classful addressing, the address space is divided into five classes:A, B, C, D, and E. We can find the class of an address when the given address is in binary notation or dotted-decimal notation. Example 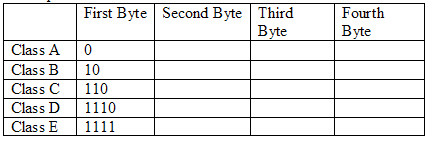
|
|
Find the error, if any, in the following IPv4 addresses.a. 200.56.045.78
b. 22.34.7.8.20
c. 75.45.279.14
d. 11100010.23.24.66
Solution
a. There must be no leading zero (045).
b. There can be no more than four numbers in an IPv4 address.
c. Each number needs to be less than or equal to 255 (279 is outside this range).
d. A mixture of binary notation and dotted-decimal notation is not allowed.
|
|
Describe how many types are wireless transmission?In general we can divide five types of wireless transmission
1. The Electromagnetic Transmission
2. Radio Transmission
3. Microwave Transmission
4. Infrared Transmission
5. Light Transmission
1. The Electromagnetic Transmission
When electrons move, they create electromagnetic waves that can propagate through space and in a vacuum. The electromagnetic waves can be broadcast efficiently and received by a receiver some distance away.
2. Radio Transmission
Radio waves are easy to generate, can travel long distances, and can penetrate buildings easily, so they are widely used for communication. These waves can travel in all directions.
3. Microwave Transmission
Microwaves travel in a straight line, so if the towers are too far apart, the earth will get in the way. Thus, repeaters are needed periodically. The higher the towers are, the farther apart they can be. Unlike radio waves at lower frequencies, microwaves do not pass through buildings well.
4. Infrared Transmission
It is used for short-range communication. The remote controls used for televisions, VCRs, and stereos, use infrared communication. They are relatively directional and can not pass through solid objects.
5. Light Transmission
These types of wave can easily effected by wind and temperature changes. They normally work well on sunny days.
|
|
Explain Random Excess Method.In Random Excess Method, any station can send the data at any time without the permission of other station. At any time, if a station has information to send to other station, it uses a specific method defined by the protocol to make a decision on whether or not to send. There is no scheduled time for a station to transmit the data that is why it is called Random Excess Protocol. Random protocol has the following types. 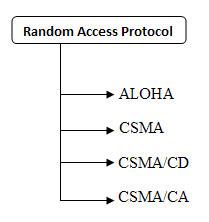
|
|
Explain Channelization in networks.Channelization is a multiple-access method in which the available bandwidth of a link is shared in time, frequency, or through code, between different stations. There are three basic approaches to achieve channelization. 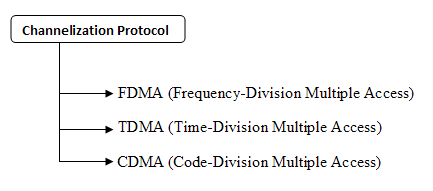
|
|
Describe FDMA and TDMA in short.In frequency-division multiple access (FDMA), the available bandwidth is divided into frequency bands. Each station is allocated a band to send its data. Different frequency bands are used by different stations. In time-division multiple access (TDMA), the stations share the bandwidth of the channel in time. Each station is allocated a time slot during which it can send data. Each station transmits its data in is assigned time slot. 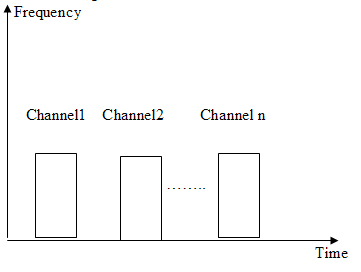
|
|
Explain CDMA in wireless networks.CDMA differs from FDMA and TDMA because only one channel occupies the entire bandwidth of the link and also there is no timesharing. In CDMA a code is available for every station wanting to send the data. In this protocol the assigned codes have two properties.
1. If we multiply each code by another, we get zero.
2. If we multiply each code by itself, we get the number of stations.
So suppose there are three stations and code and data are (c1, d1), (c2, d2), (c3, d3) respectively. The data that go on the channel are the sum of all these terms. Any station wanting to receive data from one of the other two, multiplies the data on the channel by the code of the sender. For example, suppose stations 1 and 2 are talking to each other. Station 2 wants to hear what station I is saying. It multiplies the data on the channel by cl the code of station 1.
Because (cl . cl) is 3, but (c2 . cI) and (c3 . cI) are all Zero, station 2 divides the result by 3 to get the data from station 1.
|
|
Describe the functionality of data link layer.Data Link Layer is the second layer from the bottom in OSI model. This layer has two main functions
- Data link control
- Media access control.
Data link control provides the functionality of include framing, flow and error control that provide smooth and reliable transmission of frames between nodes. Media Access Control (MAC) handles the sharing of link.
|
|
Explain Stop-and-Wait Automatic Repeat Request for noisy channel.In this protocol the sending device keeps a copy of the last frame transmitted until it receives an acknowledgment for that frame. A data frames uses a sequence number; an ACK frame uses an acknowledgment number. The sender has a control variable, which we call Sn (sender, next frame to send), that holds the sequence number for the next frame to be sent (0 or 1).
|
|
What is the difference between Pure ALOHA and Slotted Aloha protocol?In Pure Aloha, station can send data in a continuous time manner whereas in Slotted Aloha, time is divided in slots. Pure ALOHA doesn't check whether the channel is busy before transmission. In slotted ALOHA, a frame can be sent only at fixed times, whereas in pure ALOHA, you can send any time. Pure ALOHA has a vulnerable time of 2 x Tfr. Whereas in Slotted ALOHA vulnerable time = Tfr {Tfr: Average transmission time for a frame}.
|
|
Differentiate between hub and switch.a.) Hub is a layer 1 device while Switch is layer 2 device.
b.) Hub works on single collision and single broadcast domain while switch works on per port collision and single broadcast domain.
|
|
What is FQDN?- FQDN is the abbreviation for Fully Qualified Domain Name.
- It contains both the hostname and a domain name.
- It uniquely identifies a host within a DNS hierarchy
|
|
Tell us something about LMHOSTS files.- It is a text file that resolves NetBIOS names to IP addresses.
- It can be compared with the HOSTS file which is a static method of resolving domain names into IP addresses.
- LMHOSTS files must be manually configured and updated.
|
|
What are the main qualities of an effective and efficient network?a. Performance
b. Reliability
c. Security
|
|
What are 10Base2, 10Base5 and 10BaseT Ethernet LANs?10Base2 -
- It is an Ethernet term which means a maximum transfer rate of 10 Megabits per second that uses baseband signaling, with a contiguous cable segment length of 100 meters and a maximum of 2 segments.
10Base5
- It is an Ethernet term meaning a maximum transfer rate of 10 Megabits per second that uses baseband signaling, with 5 continuous segments not exceeding 100 meters per segment.
10BaseT
- It is an Ethernet term meaning a maximum transfer rate of 10 Megabits per second that uses baseband signaling and twisted pair cabling.
|
|
What is anonymous FTP? What is its use?- It is an FTP that enables the users to connect to a host without a valid login and password.
- The login used is anonymous or guest, with the password usually requesting the user's ID.
- It enables a large number of users to access the files on the host without needing to set up a login for all of them.
- It exercises a strict control over the areas an anonymous user can access.
|
|
Which factors mark the reliability of the network?a. Frequency of failure
b. Downtime / Time taken for recovery.
|
|
Name the factors that tell us about the security of the network.a. Virus attacks on the system.
b. Unauthorized access to the system.
|
|
Define Bandwidth and Latency?- Bandwidth/ Throughput – It means the number of bits which can be transmitted over the network in a specified time.
- Latency – It is the time taken by a message to travel from one side to another.
Bandwidth and latency describe the performance of a network.
|
|
What is point to point link?- Direct connection between two computers on a network is called as point to point link.
- No other network devices other than a connecting cable are required for point to point connection.
- The cable connects the NIC card of both the devices.
|
|
When is a switch said to be congested?- Sometimes a switch receives the packets faster than they can be accommodated in the shared link. These packets are stored in the memory for sometime.
- However, after sometime the buffer space will exhaust and some packets will start getting dropped off.
- The switch is called as congested in this state.
|
|
Explain a.) Uni-casting, b.) Multicasting and c.) Broadcastinga.) Uni-casting - Message is sent from a source to a single destination node.
b.) Multicasting - Message is sent from a source to some subsets of other nodes.
c.) Broadcasting - Message is sent from a source to all the nodes in the network.
|
|
What are the various types of Multiplexing?The various types of multiplexing are:
a. Frequency Division Multiplexing (FDM)
b. Time Division Multiplexing (TDM)
i. Synchronous TDM
ii. Asynchronous TDM
c. Wave Division Multiplexing (WDM)
|
|
Which layers of OSI are referred to as network support layers?The following 3 layers of OSI are referred to as network support layers:
a. Physical Layer
b. Data link Layer and
c. Network Layers
|
|
Which layers of OSI are referred to as user support layers?The block of user support layers consists of:
a. Session Layer
b. Presentation Layer and
c. Application Layer
|
|
What does the Data Link Layer do?- The Data Link Layer transforms the physical layer to a reliable link.
It takes care of:
a. Node to node delivery.
b. Framing
c. Physical Addressing
d. Flow Control
e. Error Control
f. Access Control
|
|
What is NIC?- NIC stands for Network Interface Card.
- It is a peripheral card attached to a PC to helps it connect to a network.
- The MAC address of the card helps the network in identifying the PC.
|
|
What are the responsibilities of Network Layer?- The Network Layer aids in source-to-destination delivery of packet across multiple networks.
- It performs:
a. Logical Addressing
b. Routing
|
|
Name the various error detection methods.The various error detection methods are:
a. Vertical Redundancy Check (VRC)
b. Longitudinal Redundancy Check (VRC)
c. Cyclic Redundancy Check (VRC)
d. Checksum
|
|
What is Bit Stuffing?- Bit stuffing means adding one extra 0 whenever five consecutive 1s follow a 0.
- This is done so that the pattern 0111110 is not mistaken for a flag.
|
|
How does dynamic host configuration protocol aid in network administration?- In a large set up where it is difficult to manually configure the IP address of each system, dynamic host configuration protocol comes very helpful.
- Using this protocol, the administrator can create a pool of IP addresses which are called scopes. These can be then dynamically assigned to the systems.
|
|
Describe the Packet Format of ARP (Address Resolution Protocol)?The fields of the packet format of ARP are as follows:
-Hardware type: It is a 16-bit field . Each LAN has been assigned an integer based on its type. For example, Ethernet is given the type 1.
-Protocol type: This is a 16-bit field defining the protocol. For example, the value of this field for IPv4 protocol is 0800.
-Hardware length: This is an 8-bit field defining the length of the physical address in bytes. For example, for Ethernet the value is 6.
-Protocol length: This is an 8-bit field defining the length of the logical address in bytes. For example, for IPv4 protocol the value is 4.
-Operation: This is a 16-bitfield defining the type of packet. Two packet types are defined: ARP request (1), ARP reply (2).
-Sender hardware address: This is a variable-length field defining the physical address of the sender. For example, for Ethernet this field is 6 bytes long.
-Sender protocol address: This is a variable-length field defining the logical (for example, IP) address of the sender. For the IP protocol, this field is 4 bytes long.
-Target hardware address: This is a variable-length field defining the physical address of the target. For example, for Ethernet this field is 6 bytes long.
-Target protocol address: This is a variable-length field defining the logical (for example, IP) address of the target. For IPv4 protocol, this field is 4 bytes long.
|
|
What are the advantages of IPv6 over IPv4?The next generation IP, or IPv6 has some advantages over IPv4 that can be summarized as follows:
- Larger Address Space: An IPv6 address is 128 bytes long where IPv4 has 32-bit address only, this is a huge increase in the address space.
- Better Header Format: IPv6 uses a new header format which simplifies and speeds up the routing process because most of the options do not need to be checked by routers.
- New Options: IPv6 has new options to allow for additional functionalities.
- Allowance for extension: In IPv6 new technologies can easily embedded.
-Support For Resource Allocation: In IPv6, flow label has been added to enable the source to request special handling of the packet. This mechanism can be used to support traffic such as real-time audio and video.
-Support For More Security: The encryption and authentication options in IPv6 provide confidentiality and integrity of the packet.
|
|
What are the different design goals of ATM?Asynchronous Transfer Mode (ATM) is the cell relay protocol.
The Design Goals of ATM are as follows:
- A technology is needed to take advantage of high rate transmission media and less susceptible to noise degradation for maximizing the data rates.
-The system must interface with existing systems and provide wide-area inter-connectivity between.
-The implementation of design must be cheaper enough so that everyone can afford it. If ATM is to become the backbone of international communications, as indeed, it must be available at low cost to every user who wants it.
-The new system must be able to work with and support the existing telecommunication hierarchies.
- The new system must be connection-oriented to ensure accurate and predictable delivery.
- One objective is to move as many of the functions to hardware as possible (for speed) an eliminate as many software functions as possible (again for speed).
|
|
In which switching physical path is present and how it is different from packet switching?- Circuit switching uses physical path for transmission of data.
- Here initially a physical connection is established between source and destination & then data is sent .
- In packet switching data is broken into small parts called packets.
- Numbered packets may take any shortest route for transmission.
- In packet switching virtual connection is made between source and destination.
|
|
Give the frame format for data link layer.- Header, payload filled, trailer are the main parts of a frame.
- Header contains the number of characters in a frame & source and desitnation address.
- Payload filled contains the data to be sent.
- Trailer is the end of packet and it also contains the starting and ending bits.
- This frame is sent to network layer.
|
|
Why acknowledged service is better?- When data is sent acknowledgement at reception of data occurs.
- If frame is lost, then error is detected and the data is sent again.
- Recovery of data takes place easily.
- It works for reliable channels where error is minimum.
- This is a time saving method and better than unacknowledged service .
|
|
What are the problems in Character count framing method.- In character count the header gives number of characters in frame.
- E.g. 2,3,4,2,5,7, 0,4
- Initially two frames will be sent as header shows 2 i.e. 3 and 4.
- Again 2 frames will be sent shown by next header and frames are 5and 7.
- 3rd Header is 0 which lead to wastage of time and bandwidth and no frame is sent.
- This leads to error and should be avoided.
|
|
Explain Echoplex- It is a method used to detect error in data link layer and is also called echo checking.
- Here reciever retransmits the data back to the transmitter after reception.
- It requires a full duplex operation for sending and receiving data.
- When data is received at the transmitter,error can be detected by the human operator .
- Its disadvantage is that it depends on humans for error detection and correction.
|
|
What is D T E-Data Terminal Equipment.- It is a Digital device than generates, transmits and recieves messages.
- Terminal here is used to show the movement of messages in and out of the terminal.
- Server and the hosts maintain data and give information to Terminals.
- Examples: TTY: Teletypewriter or Keyboard.
ATMs. Automatic Teller Machines
|
|
Explain front end processcor (FEP).- It is a type of data Terminal Equipment which is a digital device used to input data and give the required output.
- Performs data communications at host location.
- Host can communicate with all data circuits present at its server.
- The host location can also be remote from the server.
- The main advantage of FEP is it avoids slow processing.
|
|
Explain line control Unit (LCU).- Performs communication related to remote location.
- Directs the flow of data from communication channel to terminals present at remote location.
- Perform serial to parrellel data conversion at transmitter and vice-versa at reciever.
- Also perform the error detection and correction of the packets sent.
- Control characters can be inserted or deleted from the packets easily .
|
|
Explain UART.- Called Universal asynchronous receiver transmitter.
- Serial to parrallel conversion of data takes place at transmitter and vice –versa occurs at reciever.
- Start and stop bits are send with data without any clock pulses for synchronization .
- Formating of Data in Transmitter and Receiver takes place.
- Also allows Voltage level conversion at both ends. Error detection and correction and bits synchronization is possible and data is sent in form of bytes.
|
|
Explain USRT.- Called universal synchronous receiver transmitter .
- Here clocking information in form of bits is also transferred with the data.
- Here no start and stop bits are transmitted with the data.
- Parity bits are inserted and data sent in form of Blocks.
- Transmit and receive status information is send or received.
- The synchronous & asynchronous receiver transmitter can be combined forming USART.
|
|
Explain SNRM- Set normal response mode is an unnumbered command of synchronous data link control.
- This command places secondary station into normal response mode.
- In normal mode only the secondary station sends and receives information frames.
- Secondary station remains in normal mode until it receives a disconnect command.
- It is disconnected with an unnumbered acknowledgement.
|
|
What does address FF hex specify in SDLC address field.- Synchronous data link control address field is 8 bit and FF hex represents the last address.
- This address is called as the broadcast address and is common to all secondary stations.
- Frame sent with broadcast address is simultaneously sent to all other stations.
- Since it is a 8 bit address so 256 addresses are possible.
- Remaining address can also be used as unique stations or as groups.
|
|
Explain BSC- It is called as binary synchronous communications and is a type of synchronous data link protocol.
- It is sometimes also called as the bisync or bisynchronous communications.
- Each data transmission precedes a unique synchronization character (SYC).
- The message block can be poll, selection or an acknowledgement.
- The SYC character for ASCII is 16 hex.
|
|
What is block mode?- Block mode is a data transmission mode used for transmitting and receiving data.
- Here data characters are not transmitted as they are typed.
- Here initially the data characters are stored in buffers at the time of typing.
- When the sender presses Enter key then only data is transmitted.
- This set of characters stored in buffers and then sent are called blocks.
- This mode is used in multidrop data communications.
|
|
Explain BOP.- BOP is called as the bit oriented protocol used in data link protocols.
- It is used for serial bit by bit data transfer over communication channel.
- These bits can be interpreted individually or groups of bits rather fixed length groups.
- Here no dedicated data link control characters are required.
- Example: high level data link communications (HDLC).
|
|
Explain stop and wait flow control.- Here transmitter sends one message and waits for acknowledgement(ACK)
- After receiving ACK it transmits next message.
- Its main advantage is it is very simple and easy to understand.
- Its main disadvantage is its speed is very slow and time is wasted.
- Here it takes twice as long to transmit data and receive ACK.
|
|
Explain Poll/select.- It is a line discipline used for centrally controlled networks.
- Here primary station controls data and secondary station responds to instructions.
- Primary polls to secondary to determine if it has data to transmit.
- If secondary has data it responds to poll with a message and acts as a transmitter.
- If primary selects secondary, it identifies secondary as the receiver and checks if it is ready to receive data.
|
|
Explain the function of line discipline.- Line discipline is used in the data link layer which coordinates hop to hop data delivery.
- Here the hop can be a computer or a network controller.
- It also coordinates the half duplex transmission on data communication network.
- Acknowledgement discipline is used for simple networks.
- Poll/select is used for centrally controlled data networks.
|
|
Give the difference between cable and voice modems.- Cable modem operates on higher frequencies up to 850MHz.
- Cable modem uses more complex modulation and demodulation techniques than simple FSK modulation.
- Cable modems connect subscribers to cable tv and voice modem connect subscriber to the telephone network.
- Cable modem works on Bit rate of 30Mbps and voice modem works on 56000 bps.
- Cable modem works on voice and video whereas voice modem work only on voice.
|
|
What are scramble and descramble circuits used for?- Scramble circuit detects the undesirable sequence of 0 and 1 and convert them into sequence more acceptable.
- It randomizes the data to convert data back at the receiver.
- For this different algorithms are used both at the transmitter and the receiver.
- Descramble circuit generates the original sequence at the receiver.
- Example: eight consecutive 0’s are converted to alternate 0’s and 1’s which is more acceptable to the clock recovery.
|
|
Explain adaptive equalizers.- These are located in the receiver section of the modem.
- It automatically adjusts the gain and delay of the input received to compensate for the phase and amplitude impairments.
- It determines the quality of the received signal.
- It continuously vary its settings to achieve bandwidth characteristics for the circuit.
- Because of their adjusting property they are called adaptive equalizers
|
|
Issues for data interfacing in physical layer.- Raw data is to be converted into binary form 0 and 1 to be sent to the next layer.
- Different voltages are required for representing 0(0 to1.5 volts) and 1(3 to 5 volts).
- How many nano seconds a bit should last.
- How transmission may proceed from physical layer to data link layer or from communication channel to physical layer .
- How many pins network connectors may use for serial communication.
|
|
Which physical property of information is changed for transmission?- Current or Voltage of signal is changed for transmitting it in the form of zeros and ones.
- Signal broken into harmonics called frequency using Fourier transform.
- Amplitude of signals due to Fourier transform may be reduced.
- A filter is attached before the transmission medium which allows only required harmonics to pass through the medium.
- Signal at the receiver end can be reconstructed from harmonics using inverse Fourier transform .
|
|
Explain resource sharing- Different resources are attached to a computer and if they can be used by other computers in the same network it is called resource sharing.
- It is generally possible in local area networks confined to offices or institutes.
- The host requires an operating system to access the resources of the server.
- FTP called the file transfer protocol is used to provide the shared access between host and the server.
- It is cheaper, faster and easier to maintain.
|
|
Which transmission medium radiates and how it can be avoided?- Twisted pair cable radiates energy during transmission.
- Two wires present in the cable constitute an Antenna which radiates energy in all directions.
- The wires are twisted like a DNA present in human blood.
- Waves coming out from the two twisted wires are out of phase by 180 degree so they cancel out.
- Leads to no radiations and also sheath could be provided outside the cable to provide insulation.
|
|
Which category of twisted pair is mainly used.- There are up to 7 categories of twisted pair but Category 3 and 5 twisted pairs are mostly used.
- Category 3 has 2 individually insulated wires twisted together .
- 4 such twisted pairs are put together in a sheath to form the medium.
- Category 5 is same as 3 with more number of twist per cm. More the number of twists the better the communication medium .
- Leads to less cross talk and better signal transmission over longer distances.
|
|
Which transmission medium works at 2 giga bits per second.- The fiber cable sends data at rate of 2 giga bites per second.
- Cable consists of Hair like thin fiber which works on the principle of total internal reflection.
- It transmits data with speed of light and works on bandwidth up to terahertz.
- Transmitting medium is fiber of glass which is insulated on the outside.
- Advantage:Attenuation of signal is minimum.
Speed of transmission is very high.
|
|
Can infrared be used for transmission- The infrared waves can be used for short range communication in networking (up to 45 km).
- It is wireless communication so no physical medium is required to connect the transmitter and receiver .
- Works on line of sight system i.e. the transmitting and receiving antennas should be in the sight of each other.
- No government license is needed till now for this communication .
- Example :used in television ,stereos.
|
|
Compare satellite and cable medium for transmission.- Delay given by satellite during its transmission is 3 micro seconds per km.
- Delay given by cable wire is 5 micro seconds per km.
- Satellite is broadcast media placed in the geo stationary orbit around the earth.
- Satellite is used in wireless communication system and cable is used in wired communication.
- On security grounds cable is better than a satellite.
|
|
Explain Store and forward Network.- Store and forward method is used in message switching. Example: SMS
- The data sent by the sender is first stored at the server.
- Data is later forwarded from the server to the receiver.
- It may use time division multiple access for transmission i.e. the whole bandwidth is given to single user for smalltime slots.
- No physical path is required for transmission of data from sender to the receiver.
|