Maintenance
Explain method of estimating software maintenance cost.
What is software maintenance?
It is a software engineering activity which occurs during the delivery of a software product to the customer.
Methods for estimating software maintenance cost are followed:
1. Belady and lehman model:- In Belady and lehman model when effort and cost can increase exponentially then poor software development approach is used.
- The person or group uses the approach that is no longer available to perform maintenance.
The basic equation is:
M = P + ke(c-d)
where,
M is a total effort expended.
P is productive effort that involves analysis, design, coding, testing and evaluation.
K is an empirically determined constant.
c is complexity measure due to lack of good design and documentation
d is degree to which maintenance team is familiar with the software.
- In this relation, the value of 'c' is increased if the software system is developed without the use of a software engineering process.
- Here, 'c' will be higher for a large software product with a high degree of systematic structure than a small one with the same degree.
- The value of 'd' will be lower when software is maintained without understanding their structure, function and purpose.
2. Beohm Model:- A second method for estimating the cost of a software product is Boeohm method. In this method, Beohm proposed a formula for cost estimation and the cost is estimated from COCOMO model.
- The data is gathered from several projects and the formula was established in terms of effort.
- This method used a quantity called as Annual Change Traffic (ACT).
- ACT is defined as the fraction of a software product source instructions which undergo change during a year either through addition, deletion or modification.
- ACT relates to the number of change request.
ACT = KLOCadded + KLOCdeleted / KLOC total- The annual maintenance effort (AME) is calculated as:
AME = ACT * SDE
Where, SDE is software development effort in person months.
ACT is Annual change Traffic- For example, a software project required 400 person months of development effort and it was estimated that 25% of the code modified in a year.
AME = 0.25 * 400 = 100- The rough estimate should be refined by the importance factor proposed by the cost and selecting the appropriate cost multipliers.
- Using these factors, Effort Adjustment Factor calculated in the case of COCOMO model.
The modified equation is:
AME = ACT * SDE * EAF
Give various components of legacy system.
What is legacy system?- Legacy system is using a computer system, programming language, method that is developed in past instead of an upgraded version.
- It means it uses old technology, method, application program, computer system.
- This system not only includes hardware and software but also legacy processes and procedure.
- The process and procedure are the old way of doing things that are difficult to change because they depend on legacy software.
Components of legacy system:
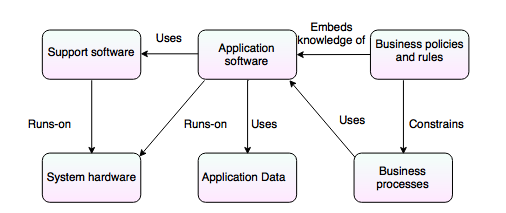 1. System hardware:
1. System hardware:- The legacy systems are written for mainframe hardware that are not available for longer period and are expensive to maintain.
- These system may not be compatible with current organizational IT purchasing policies.
2. Support software:- The legacy system depends on a range of support software from the operating system and utilities that are provided by the hardware through to the compilers used for the system development.
- These are no longer supported by their original providers.
3. Application software:- This system provides the business services that are usually composed of a number of separate program which have been developed at different time.
- Rather than the entire system sometimes the term legacy system means the application software.
4. Application data:- The data in this system is proposed by the application system.
- In most of the legacy system, huge volume of data is gathered over the lifetime of the system.
- This data is inconsistent and duplicate in several files.
5. Business processes:- To achieve some business objective these processes are used in business.
- In manufacturing company, a business process accept an order for product and sets up the manufacturing process.
- Business processes are designed around a legacy system and constrained by the functionality that it provides.
6. Business policies and rules:- Business policies and rules are the definition of how the business is carried out and constraints of the business.
- The use of legacy application system is embedded in these policies and rules.
Write a short note on Reverse Engineering.
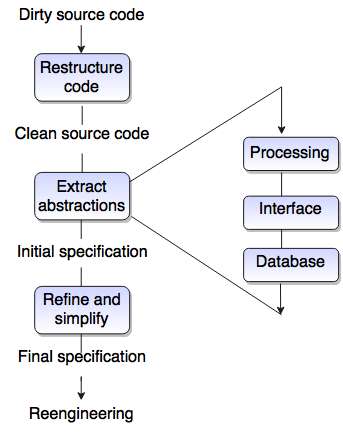
What is reverse engineering?- Reverse engineering is the process of analysis, design or knowledge information from any human made device.
- Reverse engineering is a process used to extract information from source code, but the completeness of documentation is in abstraction level.
- It is also called as back engineering.
What is the process of reverse engineering?- Process of reverse engineering follows abstraction, completeness and directionality.
- In abstraction level of reverse engineering information can be extracted from source code.
- The abstraction level is high as possible that means this process is capable of deriving procedural design representation or low level abstraction as well as high level abstraction like program and data structure information, object model, control flow model, entity relationship model.
- The completeness of this process is the level of detail that is provided at an abstraction level.
- In most of the cases when completeness decreases at that time abstraction level increases.
- Directionality of reverse engineering process extracts all information from the source code and this information is used during the maintenance activity.
 What are the uses of reverse engineering?
What are the uses of reverse engineering?- Reverse engineering is used in variety of field such as software design, software testing, programming etc.
- In software design, the programmer is allowed to add new features with or without knowing the source code of the existing software.
- It is used to crack software and media for removing content protection.
- It is used in software security.
What are the benefits of reverse engineering?- Reverse engineering is beneficial for testers to study malware code.
- Analysis of hardware for commercial and military benefits is the origin of reverse engineering.