Networking questions for Computer Science students.
What is a network? What are the different kinds of network? Explain them.
A network is a group of computers or nodes connected together. They are connected with each other by communication paths.
Types of Networks:
LAN- Local Area Network connects a group of nodes covering a small physical area.
- LAN’s are most commonly seen in offices, buildings etc.
- LAN’s enable higher transfer rate of data, smaller coverage of area and hence less wiring is required.
- Speed of LAN ranges from 10 mbps to 100 mbps.
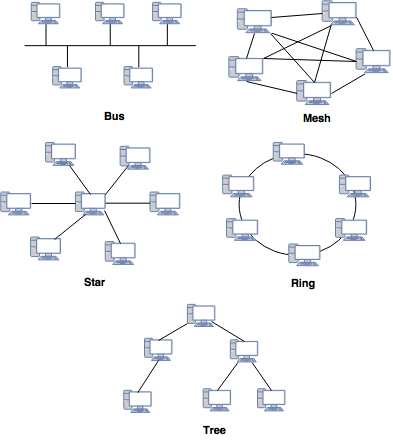
- LAN provides various network topologies. Ex. Bus, Star, Mesh, Ring, Tree, etc.
Some of these topologies are:
 WAN
WAN- Wide Area Network connects a group of nodes covering a wide area.
- WAN typically connects and allow communication between regions or national boundaries.
- The most common example of WAN is internet.
VPN- Virtual Private Network connects or link nodes in some larger area by open connections or virtual circuits in some larger network (e.g., the Internet) instead of physical wires.
- It is used for secure communication through the public internet. VPN alone may not support explicit security features, such as authentication or content encryption.
Intranet- Intranet is a set of networks under the control of a single administrative person.
- It can be considered as an internal network of an organization.
- If it is large, web servers are used to provide information to the users.
Extranet- Extranet is a network that restricts itself within a single organization.
- It can be categorized as WAN, MAN etc. however; it cannot have a single LAN. It must have a connection (at least one) with external network.
What is LAN?
- LAN is a computer network that spans in a relatively small area. Most LANs are confined to a single building or group of buildings.
- However, one LAN can be connected to other LANs over any distance via telephone lines and radio waves. A system of LANs connected in this way is called a wide-area network (WAN).
- Most LANs connect workstations and personal computers. Each node (individual computer) in a LAN has its own CPU with which it executes programs, but it also is able to access data and devices anywhere on the LAN.
- This means that many users can share expensive devices, such as laser printers, as well as data.
- Users can also use the LAN to communicate with each other, by sending e-mail or engaging in chat sessions.
- A common example of LAN, found in many business environments, links a workgroup of task-related computers, for example, engineering workstations and accounting PCs.
What's the difference Between an Intranet and the Internet?
| Internet | Intranet |
|---|
| The Internet is an open, public space network. | It is protected by a password and accessible only to employees or other authorized users. |
| Unlimited number of users. | Limited number of users. |
| Unlimited visitors traffic. | Limited visitors traffic. |
| Every computer in internet is identified by unique IP Address. Internet contains unlimited source of information and is available to all. | Every computer in Intranet is also identified by an IP Address which is unique among the computers in that Intranet. Intranet contains only specific group information |
Define the term Protocol.
- Protocol is a standard way of communicating across a network.
- It is a set of rules or procedures for transmitting data between two electronic devices, such as computers.
- A protocol is the "language" of the network.
- It is a method by which two dissimilar systems can communicate.
- There are many different types of protocol – TCP/IP, HTTP, PPP, FTP and SLIP.
What is FTP (File Transfer Protocol)?
- FTP is File Transfer Protocol.
- It is the standard mechanism provided by TCP/IP for transferring a file from one host to another.
- File Transport Protocol is a program that enables user to send and receive large portion of data through a private or public network.
- It uses the port 21 for control connection and the port 20 for the data connection.
The following figure shows the basic model of FTP.
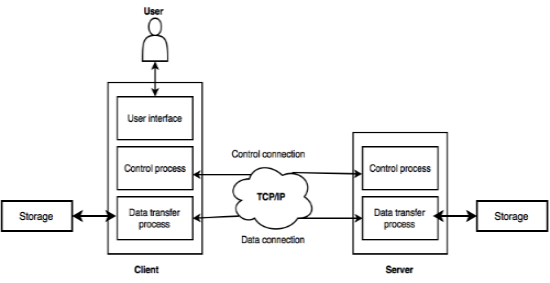
- The client has three components such as user interface, control process, and data transfer process. Server has two components such as control process and data transfer process.
- The connection made between client control process and server control process is control connection.
- The connection made between client data transfer process and server data transfer process is data connection.
- The control connection remains connected during the complete interactive FTP session.
- The data connection is opened and closed for each file transferred. It opens before transferring file and closes when the file is transferred.
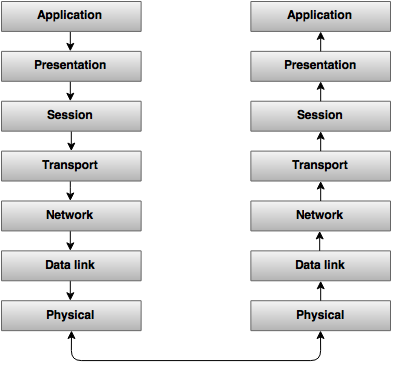
Explain the 7 Layers of OSI.
Layer 1: Physical layer
It represents all the electrical and physical specifications for devices.
Layer 2: Data link layer
It provides the functional and procedural means to transfer data between network entities and to detect and possibly correct errors that may occur in the Physical layer.
Layer 3: Network layer
The Network layer provides the functional and procedural means of transferring variable length data sequences from a source to a destination via one or more networks.
Layer 4: Transport layer
It provides transparent transfer of data between end users.
Layer 5: Session layer
It controls the sessions between computers. It connects, manages and terminates the connections between the local and remote application.
Layer 6: Presentation layer
It transforms data to provide a standard interface for the Application layer.
Layer 7: Application layer
It provides a means for the user to access information on the network through an application.
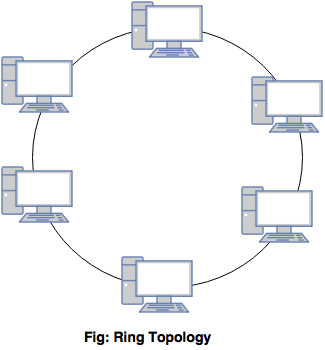
What are network topologies? Explain Ring, Bus and Star topology.
A network topology describes the layout of a network. It describes how different nodes and elements are connected to each other.
Different types of topology:
Ring- All nodes are connected with another in a loop.
- In this topology, each node has a dedicated point-to-point connection with one or more other device on either side.
- Each node is connected only to its immediate neighbors.
- Ring topology is easy to install and manage.
- To add or remove a device requires changing only two connections.
- If one single computer fails, the entire network goes down.
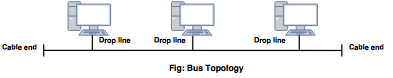
 Bus
Bus- All nodes are connected to a central and a common cable called as a back bone.
- In bus topology, the server is at one end and the clients are connected at different positions across the network.
- Easy to manage and install.
- If the backbone fails, the entire communication fails.
- Disadvantage is difficult reconnection and fault isolation.
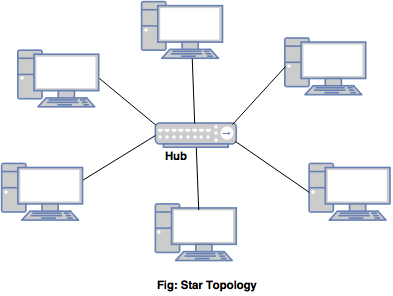
 Star
Star- All nodes are connected to a central hub.
- The communication between the nodes is through the hub.
- The dependency of entire network is on one single device, the hub.
- If the hub goes down, the entire system is dead.
- It requires more cables as compared to BUS. However if any node fails, it won’t affect the entire network.
Explain IP, TCP and UDP.
TCP- Transmission control Protocol is used to establish communication between nodes or networks and exchange data packets.
- It guarantees delivery of data packets in the order they were sent.
- Hence it is most commonly used in all applications that require guaranteed delivery of data.
- It can handle both timeouts (if packets were delayed) and retransmission (if packets were lost). The stream of data is transmitted in segments.
- The segment header is 32 bit. It is a connectionless communication protocol at the third level (network) of the OSI model.
IP- Internet protocol is used for transmission of data over the internet.
- It uses IP addresses to identity each machine uniquely.
- Message is sent using small packets. The packet contains both the sender and receivers address.
- IP does not guarantee the delivery in the same order as sent. This is because the packets are sent via different routes.
- It is a connectionless communication protocol at the third level (network) of the OSI model.
UDP- User Data Protocol is a communication protocol.
- It is normally used as an alternative for TCP/IP. However there are a number of differences between them.
- UDP does not divide data into packets. Also, UDP does not send data packets in sequence.
- Hence, the application program must ensure the sequencing.
- UDP uses port numbers to distinguish user requests. It also has a checksum capability to verify the data.
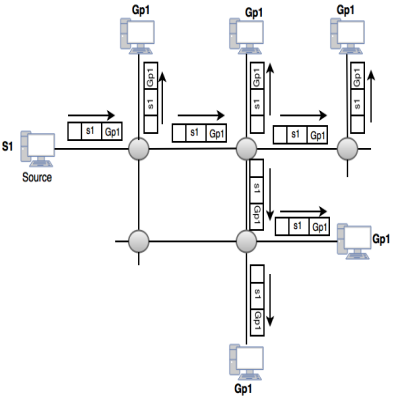
What is multicasting?
- Multicasting allows a single message to be sent to a group of recipients.
- The relationship is one-to-many.
- Emailing, teleconferencing, are examples of multicasting.
- It uses the network infrastructure and standards to send messages.
- In multicasting, the source address is a unicast address, but the destination address is a group address.
- The member of group are identified by using group address.
- The router may forward the received packet via several of its interfaces.
Figure explains the concept of multicasting.
Explain the functionality of PING.
- Ping is particularly used to check if the system is in network or not.
- It also gives packet lost information. In windows, ping command is written as ping ip_address.
- The output returns the data packets information.
- The number of packets sent, received and lost is returned by PING.
- It is a basic internet program which allows the user to verify an IP address exists and accepts request.
- They are used for troubleshooting the test connectivity and determine the response time.
What is a MAC address?
- A Media Access Control address is a unique identifier that is assigned to the network adapters or NICs by the manufacturers for the purpose of identification and used in the Media Access Control protocol sub layer.
- It is a 12 digit hexadecimal number. Hexadecimal digits can include only the numbers 0-9 and letters A-F.
- A MAC address usually encodes the registered identification of the manufacturer, if the address is assigned by the manufacturer.
- It sometimes is also called as Ethernet Hardware Address / physical address / adapter address.
Explain Spanning-Tree protocols.
- The Spanning Tree Protocol is a network protocol that provides a loop-free topology for any bridged Ethernet local area network.
- It is implemented in LAN connections.
- On a mesh topology, a set of spanning tree algorithms were developed for prevention of redundant transmission of data along with intermediate hops between a source and a destination host.
- In the absence of spanning trees, a mesh network is flooded and rendered unusable by messages by circulating within a loop that is infinite, between hosts.
- An algorithm used in transparent bridges which determines the best path from source to destination to avoid bridge loops.
- At the time of STP initialization in a network, its first action is to utilize the Spanning Tree Algorithm for selection of a root bridge and a root port.
- The root bridge is the network which has lowest-value bridge identifier.
- All the switches on the network use Bridge Protocol Data Units to broadcast the bridge IDs to the other switches in that network.
- Soon after selection of the root bridge, determination of the root ports on all other bridges is done.
What is the use of IGMP protocol?
- Internet Group Management Protocol is a communication protocol which allows internet hosts to participate in multicasting.
- The IGMP messages are used to learn which hosts is a part of which multicast groups.
- The mechanism also allows a host to inform its local router that it wants to receive messages.
What are Ping and Tracert?
- Ping and tracert are the commands used to send information to some remote computers to receive some information.
- Information is sent and received in small blocks of data, called packets.
Ping- Ping is particularly used to check if the system is in network or not.
- It also gives packet lost information.
- In windows ping command is written as ping ip_address.
Tracert- Tracert is called as trace route.
- It is used to track or trace the path the packet takes from the computer where the command is given until the destination.
- It will list all the routers it passes through until it reaches its destination.
- In windows ping command is written as tracert ip_address.
Explain RSVP. How does it work?
- Resource Reservation protocol is used to reserve resources across a network.
- It is used for requesting a specific Quality of Service (QoS) from the network.
- This is done by carrying the request (that needs a reservation of the resource) of the host throughout the network.
- It visits each node in the network.
- RSVP uses two local modules for reservation of resources.
- Admission control module confirms if there are sufficient available resources while policy module checks for the permission of making a reservation.
- RSVP offers scalability. On a successful completion of both checks RSVP uses the packet classifier and packet scheduler for the desired QoS requested.
Explain the concept of DHCP.
- DHCP is a Dynamic Host Configuration Protocol.
- It is used to assign dynamic IP addresses to computers in a network.
- Using DHCP computer has a different IP addresses every time it connects to a network.
- In some system the IP addresses can change while the system is still connected. It means that DHCP leases out the IP address to the computer for some time.
- It is used to control the network configuration of a host through a remote server.
- DHCP provides static and dynamic address allocation that can be manual or automatic.
- It is an excellent alternative to the time consuming manual configuration of network setting for a host or a network device.
- It works on a client server model.
- It is a protocol which has its own set of messages.
- The advantage of the DHCP server is that the IP configuration gets automatically configured to the client machine.
- To manage the IP address a software can be used rather than an administrator.
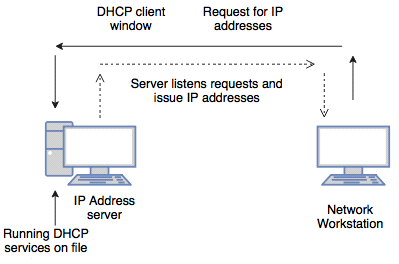
What are the differences between a domain and a workgroup?
| Domain | Workgroup |
|---|
| In a domain one or more computer can be a server to manage the network. | In a workgroup all computers are peers that have no control on each other. |
| In this user doesn't need an account to login on a specific computer if an account is available on the domain. | In a work group user needs to have an account for every computer. |
| In domain all computers can be a part of different local networks. | In a work group all computers need to be a part of the same local network. |
| In domain, centralized administration. | In workgroup, no centralized authorization. |
| The computers can be on different local networks in a domain. | All the computers must be on the same local network or subnet in a workgroup. |
| A domain user provides a password each time they access the domain. | A workgroup is not protected by a password. |
| In domain, thousand of computer. | In workgroup, typically no or more than twenty computers. |
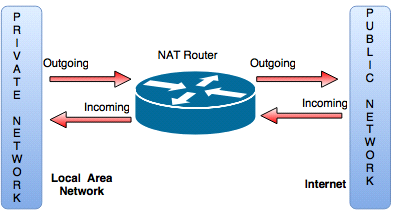
Explain how NAT works.
- NAT is a Network Address Translation or Network Address Translator.
- It is a virtualization of IP addresses.
- It translates an IP address used in a network to another IP address known within another network.
- It is an internet standard that allows a local area network to use one set of IP addresses for internet traffic and a second set of addresses for external traffic.
- It prevents malicious activity initiated by outside hosts from reaching local hosts by being dependent on machine in the local network to initiate any connection to host on the other side of the router.
- A NAT router is responsible for translating traffic that is coming and leaving the network.
- A NAT table maintains global to local and local to mapping of IP addresses.
- In pooled NAT, outside pooled IP addresses are used and shared by inside devices when connected to the internet.
- It helps to improve security and decrease the number of IP addresses.
What is PPP protocol? Explain PPP packet format?
- PPP means Point to Point protocol.
- It helps to communicate between two computers over a serial cable, phone line or fiber optic lines.
- For example, Connection between an Internet Service Provider and a host.
- It provides authentication.
- It operates by sending request packets and waiting for acknowledging packets that either accept, reject or try to change the request.
Packet format:
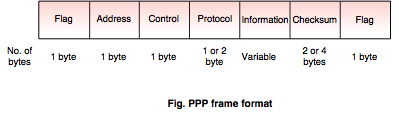 Flag field: 1 byte:
Flag field: 1 byte: It indicates the beginning and end of the frame.
Address field: 1 byte: Address is the broadcast address that means all the stations are accepting this frame.
Control field: 1 byte: It controls the acknowledgement of the frame.
Protocol field: 1 or 2 bytes: PPP receiver checks the frame for correctness and then pass the encapsulated data to the appropriate protocol.
Information: The length of the field is variable. The default maximum length of this field is 1500 bytes. This can be changed when the link is first configured.
Checksum: The length is either 2 bytes or 4 bytes. It is used to detect bit error in transmitting frames.
What is IP spoofing and how can it be prevented?
What is IP spoofing?- IP spoofing is a mechanism used by attackers to gain unauthorized access to a system.
- It refers to connection hijacking through a fake internet protocol address.
- In IP spoofing the intruder sends messages to a computer with an IP address indicating that the message coming from the trusted host.
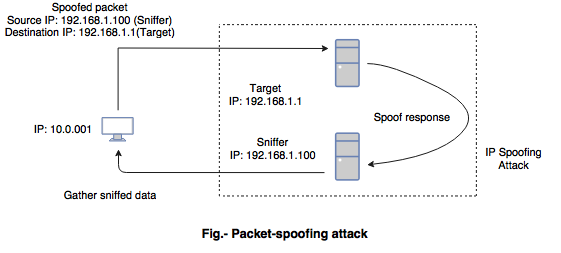 Prevention of IP spoofing:
Prevention of IP spoofing:- To prevent IP spoofing, authentication is used on the basis of key exchange between the user and the machine on a network.
- Enable the encryption session on the router so that the trusted host can securely communicate with a local host.
- It uses an access control list to deny private IP addresses on the interface.
- The filtering is implemented for the inbound and outbound traffic.
- Configure the router, switches to reject outside packets.
Explain IP datagram, Fragmentation and MTU.
IP datagram- The format of data that is recognized by IP is called an IP datagram.
- IP datagram can be used to describe a portion of IP data.
- It consists of the IP header and data.
- IP header consists of the source IP address and destination IP address.
- The field in datagram except the data have specific roles to perform the transmission of data.
- Every field in the datagram has a fixed size except for the IP option field which is 20-60 bytes in length.
- Total length of IP the IP datagram format is 32 bits.
- The various fields of datagram, such as version, Internet header length (IHL), Type Of Service(TOS), Total length, Identification, flag, fragment offset, Time to live, protocol, header checksum, source address, destination address, option, padding, data.
MTU- MTU is a Maximum Transmission unit.
- It is the size of the largest packet that a communication protocol forwards out to the interface.
- The size is fixed by some standard or decided at the time of connection.
Fragmentation- Fragmentation is the process of breaking the IP packets into smaller pieces.
- It is needed when the datagram is larger than the MTU.
- Each fragment becomes an IP datagram itself and travels independently from source.
- The process of re-assembling the whole datagram by the destination host's IP datagram from the fragments before delivering to the transport layer is called as re-assembly of the fragment.
What is an application gateway?
- An application gateway is an application program that runs on a firewall between two networks.
- An application gateway is also known as proxy.
- It is used for establishing a connection between client programs and destination service.
- The client is negotiating with the gateway server to communicate with the service destination.
- The proxy establishes the connection with the destination behind the firewall and it works on behalf of the client and also hide and protect computer on the network.
- It creates two connections: one between the client and the gateway or proxy server and one between the gateway and the destination.
Explain circuit level gateway.
- A circuit level gateway is a firewall.
- They work at the session layer of the OSI model or the transport layer of TCP/IP.
- Circuit level gateways are used for the handshaking between packets to determine if a requested session is legitimate.
- The advantage of a circuit level gateway is to hide the information about protected and private network.
What is 'Gateway of Last Resort'?
- Gateway of resort is also a default route.
- It is a route used by the router at the time when no route exists to transmit the IP packet.
- These known routes are present in the routing table, and if any route is not known by the routing table then it is forwarded to the default route.
- Each router receives the packet, and treat the packet in the same way, if the route is known then the packet will be forwarded to the known route.
Define client and server.
Client- A client is an application that runs on a personal computer or workstation and relies on a server to perform operations.
- A client is the requesting program or user in a client- server relationship.
Server- A server is a computer program that provides services to other computer programs in the same or another computer.
- A server is a program that awaits and fulfills requests from a client program in the same or another computer.
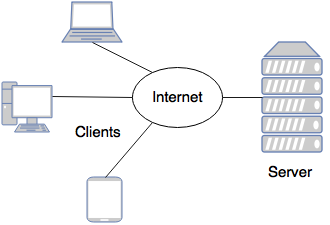
- In the above figure the clients communicating with a server via the internet.
What is soft handoff?
- A handoff is the process of transferring a phone call in progress from one base station to another base station without interruption of the call.
- Soft handoff is used in CDMA technology.
- In soft handoff, a phone actively connected to the multiple base stations simultaneously in a considerable length of time.
What are the physical characteristics of the fiber optic cable?
- Fiber optic cable supports voice, video and data.
- It produces high bandwidth, in the range 100 Mbps to 1 Gbps.
- Segment length of the fiber optic cable transmits data signals over larger distances.
- It provides security because no electric signals are passed through these type of cable.
- The cost is higher than the other type of cable.
What is static router?
- Static routing is the manual configuration and selection of a network route and it managed by the network administrator.
- This routing tables are changed or updated manually only by the administrator.
- The static router provides additional routing information to the routers.
- They are normally implemented in those situations when the choices in route selection are limited or there is no default route available.
- A static routing is used if only a few devices are available for route configuration and in future there is no need to change the route.
- Static routing is used for small networks that require only one or two routes.
- It helps in transferring the routing information from one routing protocol to another.
What is hub and state the types of hub?
What is hub:- The networks require a central location to bring media segment together and this central location is called as a hub.
- It is a networking device which receives a signal from the source, amplifies it and sends it to the multiple computers or destination.
- The hub organizes the cables and transmits incoming signals to the other media segment.
- A hub joins multiple computers or other network devices together to form a single network segment.
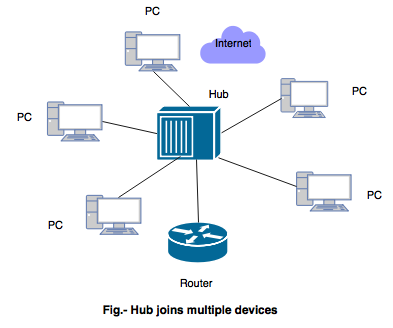 There are three types of hub:
1) Passive hub
There are three types of hub:
1) Passive hub- Passive hub works like a simple bridge.
- It is just a connector.
- It creates a connection between various devices and combines the signals of the network segment.
- This type of hub is the part of transmission media and the location in the internet model is below the physical layer.
- It receives a signal and then transfers to multiple devices.
2) Active hub- An active hub is a hub that amplifes or regenerate the information of the signal.
- It is also known as a multiport repeater.
- The distance between devices increased by using the active hub.
- An active hub is expensive than passive hub.
3) Intelligent hub- Intelligent hub perform task of both active and passive hubs.
- It also performs tasks like bridging and routing.
- It makes the performance of whole network fast and efficient because it increases the speed and effectiveness of the total network.
- An advantage of this hub is that all the transmission media segment is connected permanently only when a signal is sent to a device.
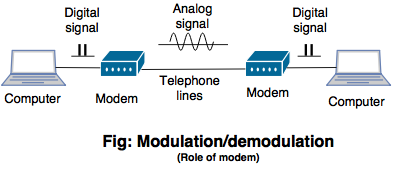
What is the role of a modem in transmission?
- The modem is known as Modulator and Demodulator.
- Modem plays an important role in data transmission from one computer to another computer network through telephone lines.
- The modem must be present in both the systems source and destination while transferring the data.
- It means both the sender and receiver must have a modem.
- If the sender does not have a modem then it will not able to send the data to the receiver.
- If the receiver does not have a modem then it will not be able to receive the data from the sender.
- Modem plays an important role to convert digital signals into anolog signals and viceversa.
- The converted analog signals are transferred from source to destination using telephone lines as a transmission channel.
- At the destination modem again converts the analog signal to digital signals.