Software Engineering and Web technologies questions and answers
(1) Each of the modules A and B shown in the figure below has cyclomatic complexity 10. The cyclomatic complexity of the sequential integration of A and B is 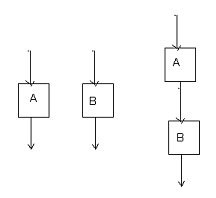
(A) 20
(B) 22
(C) 19
(D) 10
View Answer / Hide Answer(2) For the good software requirement specifications (SRS) document(A) Goals of implementation are not desired.
(B) Algorithm for software implementation is not desired
(C) Non-functional requirements are not desired
(D) Functional requirements are not desired
View Answer / Hide AnswerANSWER: Algorithm for software implementation is not desired
(A) Ping
(B) E-mail
(C) Web browsing
(D) Internet chat
View Answer / Hide Answer(4) Match the following: List I List II
a. Service oriented description p. Interoperability
b. Heterogeneous communicating system q. BPMN
c. Information representation r. Publish-find-bind
d. Process description s. XML
(A) a – q, b – p, c – s, d - r
(B) a – r, b – p, c – s, d - q
(C) a – r, b – s, c – p, d - q
(D) a – r, b – p, c – q, d - s
View Answer / Hide AnswerANSWER: a – r, b – p, c – s, d - q
a. The context diagram should depict the system as a single bubble.
b. External entities should be identified clearly at all levels of DFD’s
c. Control information should not be represented in a DFD.
d. A data store can be connected either to another data store or to an external entity.
From the statements a, b, c, and d the statements that holds true are
(A) a, b and d
(B) b and d
(C) a and c
(D) Only d
View Answer / Hide Answer(6) Three statements about the cyclomatic complexity of the control flow graph as a program module are given below:I) The cyclomatic complexity of a modules level to maximum number of linear independent circuits in a graph.
II) The cyclomatic complexity of a module is the addition of the number of number of decisions in the module and the one where a decision is effectively any conditional statements in the
module.
III) The cyclomatic complexity can also be used as number of linearly independent paths that should be tested during path coverage testing.
The statements that hold true for the cyclomatic complexity is
(A) II and III
(B) I and II
(C) I and III
(D) I, II and III
View Answer / Hide Answer(7) A software for digital signal processing which is expected to have 40000 lines of code needs to be developed by a company. This software is to be developed using the basic COCOMO model and for this the company needs to determine the effort in person-months. For the software development on the embedded system, the multiplicative factor for this model is 2.8 and the exponentiation factor is 1.20. The estimated effort in person month is(A) 287.47
(B) 950.35
(C) 234.25
(D) 122.5
View Answer / Hide Answer(8) We have different modules of software whose coupling is categorized as follows:a. Content coupling
b. Common coupling
c. Control coupling
d. Stamp coupling
e. Data coupling
Which one of the following option indicates the coupling between modules ranked in the order of strongest (least desirable) to weakest (most desirable)?
(A) b, d, a, c, e
(B) a, c, e, b, d
(C) e, d, c, b, a
(D) a, b, c, d, e
View Answer / Hide Answer(9) Consider the program given below: The number of rows in each column and the number of columns in each row are
(A) <2, 3, 2> and <2, 3, 2>
(B) <2, 2, 3> and <2, 2, 3>
(C) <3, 2, 3> and <3, 3, 2>
(D) <3, 2, 2> and <3, 2, 3>
View Answer / Hide AnswerANSWER: <2, 3, 2> and <2, 3, 2>
For questions 10 and 11 refer to the data given below:
Void fndrep (char * p, char * oldarr, char * newarr)
{
for (int j = 0; j<5; j ++)
for (int k = 0; k<3; k++)
if (p[j] == oldarr[k]; p[j] = newarr
[k];
}
Array p contains certain character string, which is to be found and replaced by using the procedure given above. Oldarr contains the characters to be replaced while array newarr
contains their respective replacement characters. Length of the array p is fixed and it contains five characters while arrays oldarr and newarr contains three characters each. However the
procedure is flawed.
The above procedure is to be tested with the following test cases given below:
I. oldarr = abc, newarr = dab
II. oldarr = cde, newarr = bcd
III. oldarr = bca, newarr = cda
IV. oldarr = abc, newarr = bac
(10) If the tester carries out the testing of the program on all input strings of five characters a, b, c, d and e with duplicates allowed using these test cases, the number of test cases
that will be able to capture the flaw is(A) 1
(B) 2
(C) 3
(D) All 4
View Answer / Hide Answer(11) Out of the four test cases, the test cases that will be successful in exposing the flaw if array p is made to hold the string abcde is(A) Only IV
(B) II and IV
(C) III and IV
(D) I and III
View Answer / Hide Answer(12) Match the following: List I List II
a. Requirement capture p. Module development and integration
b. Design q. Domain analysis
c. Implementation r. Structural and behavioral modeling
d. Maintenance s. Performance tuning
(A) a – q, b – r, c – p, d - s
(B) a – s, b – r, c – p, d - p
(C) a – q, b – s, c – p, d - r
(D) a – r, b – p, c – q, d - s
View Answer / Hide AnswerANSWER: a – q, b – r, c – p, d - s
(13) Begin
if (p = q)
{
S1;
Exit;
3
}
else if(r = s)
{
S2
}
else
{
S3;
Exit;
3
}
S4;
end
Let T1, T2, T3 and T4 be the test cases expressed in terms of the properties satisfied by the values of variables p, q, r and s whose exact values are not given. S1, S2, S3 and S4 are the
statements.
T1: p = q = r = s
T2: p ≠ q ≠ r ≠ s
T3: p = q and r != s
T4: p != q and r = s
The test cases that ensures coverage of the statements S1, S2, S3 and S4 is
(A) T1, T2 and T4
(B) T3 and T4
(C) T1 and T4
(D) T2 and T3
View Answer / Hide Answer(14) We have an HTML form that is to be designed to enable purchase of office stationary. For the items that are selected mark it with check. Submit button is to be pressed ones the credit card details are filled. Assuming that security is handled in a way that is transparent to the form design, the option that would be appropriate for sending the data to the server is (A) Only POST
(B) Only GET
(C) Either GET or POST
(D) Neither GET nor POST
View Answer / Hide AnswerANSWER: Either GET or POST
(A) Response and session only
(B) Session and request only
(C) Request and response only
(D) Session, request and response
View Answer / Hide AnswerANSWER: Session and request only
(A) FTP, HTTP, SMTP
(B) HTTP, FTP, SMTP
(C) SMTP, HTTP, FTP
(D) HTTP, SMTP, FTP
View Answer / Hide Answer(17) Which one of the following statement about HTTP is false?(A) It can be used to test the validity of a hypertext links
(B) It allows information to be stored in a URL
(C) It runs over TCP protocol
(D) It describes the structure of web pages
View Answer / Hide AnswerANSWER: It describes the structure of web pages
(A) Display the client time as part of the page
(B) Embed web objects from different sites into the same page
(C) Refresh the page automatically after a specified interval
(D) Upon download automatically redirect to another page
View Answer / Hide AnswerANSWER: Display the client time as part of the page