ISRO Computer science placement paper
1. The Djikstra’s algorithm finds its use in?
A. Calculating a link state database
B. Calculation of routing tables
C. Flooding the internet with information
D. Creation of LSAs
2. Which of the below mentioned models can be applied for the use of software reliability?
A. Rayleigh
B. COCOMO
C. Musa
D. Waterfall
3. For the UML diagram representing a class which of the following stands true?
A. State may be considered irrelevant
B. State may be represented as an attribute
C. State cannot be represented
D. State is represented as an operation result
4. The IP addresses 224.0.0.0 to 239.255.255.255 are:
A. Reserved for future addressing purposes
B. Used for multicasting
C. Reserved for broadcasting
D. Reserved for loopback
5. Which of the below options has IEEE 802.11 as a standard?
A. Bluetooth
B. WLAN
C. Wireless broadband
D. Ethernet
6. What does a physical DFD specify?
A. Which processes are to be used
B. Which data is to be generated
C. What is done by each person in an organisation
D. Data is generated by whom and is processed by whom
7. Which of the below mentioned options cannot be considered as a valid approach to Software Process Assessment?
A. ISO 9001: 2000
B. IEEE 2000: 2001
C. SPICE (ISO/IEC 15504)
D. Process improvement for standard CMMI assessment
8. In case host at network A sends a message to network B host, which address will be considered by the router?
A. Subnet Mask
B. Physical
C. IP
D. Port
9. For which of the following is SSL not responsible?
A. Data Integrity Protection
B. Secret Communication
C. Error Detection and Correction
D. Mutual authentication of server and client
10. What is the internet standard of certificates?
A. X.25
B. X.509
C. X.409
D. X.301
11. Hashed message is signed by the sender by making the use of?
A. Receiver’s public key
B. Receiver’s private key
C. Sender’s private key
D. Sender’s public key
12. There is an email which contains a birthday greeting which is textual, a song and a cake picture with no particular order. What is the content type of this email?
A. Multipart/Digest
B. Multipart /Parallel
C. Multipart/Mixed
D. Multipart /Alternative
13. Which of these specifies a rule in limited entry decision table?
A. Columns of the table which includes the conditions provided by the stub
B. Column of table which consists of conditional entries and corresponding action entries
C. Rows of table which contain action entries
D. Rows of table which contain condition entries
14. Let X denote an adjacency matrix provided in a graph G which includes no self loops. The entries which are available on the principle diagonal X can be written as?
A. Different
B. Both zeroes and ones
C. All ones
D. All zeroes
15. Which of these cannot be considered as a feature of WAP 2.0?
A. Push and Pull Model
B. Hashing
C. Multimedia messaging system
D. Interface provided to a storage device
16. Which of the below mentioned options is not a UML Diagram?
A. Swimlane Diagram
B. Class Diagram
C. Analysis Diagram
D. Use Diagram
17. Which of these is a feature of Feedback queues?
A. They are remarkably simple to implement
B. They are used in regard to real time tasks
C. They require manual intervention for proper implementation
D. They are used to dispatch tasks in accordance to execution characteristics
18. What is the Silly Window system related to?
A. Interface Problem
B. Degradation in TCP performance
C. File transfer protocol
D. Error in course of transmission
19. Which of these is an example to all loops being executed at boundaries?
A. White box Testing
B. Recovery Testing
C. Alpha Testing
D. Black box Testing
20. In RAID level programs which of the following provide the highest Data Transfer Rate?
A. RAID 5
B. RAID 4
C. RAID 3
D. RAID 1
21. Which program language gives rise to garbage collection automatically?
A. C++
B. C
C. Fortran
D. Lisp
22. Which of the following options mentioned below stand true in case of a Two phase commit protocol?
A. It ensures serializability
B. It detects deadlock
C. It prevents deadlock
D. It recovers the machine from deadlock
23. Which of the following options respectively represent Merge sort’s Average case and Worst case complexities?
A. O(n
2), O(n
2)
B. O(n
2) O(nlog
2n)
C. O(nlog
2n ) O(n
2)
D. O(nlog
2n) O(nlog
2n)
24. In a sorted array of n elements how much is the time taken by a binary search algo to search a key inn sorted array of n elements?
A. O(log
2n)
B. O(n)
C. O(nlog
2n)
D. O(n
2)
25. Identify Fibonacci Series?
A. 1, 3, 5, 7,11, 15
B. 0, 1, 1, 2, 3, 5, 8, 13, 21
C. 0, 1, 3, 7, 17
D. 1,2, 4, 9, 16, 25, 36
26. A view of data base which finds its utility in application program will be called a?
A. Virtual Table
B. Subschema
C. Schema
D. None
27. Which of the following provides an extract specified columns from inside a table?
A. Project
B. Substitute
C. Join
D. Project
28. A computer stores what in the Big Endian system?
A. MSB of a data represent smallest memory address of a data unit
B. MSB of a data represent largest memory address of a data unit
C. LSB of a data represent largest memory address of a data unit
D. LSB of a data represent smallest memory address of a data unit
29. Selection sort algorithm design technique is an example for the:
A. Backtracking
B. Dynamic Programming
C. Divide and Conquer
D. Greedy method
30. Which of these is not explained by Armstrong’s interference rule?
A. Reflexivity
B. Augmentation
C. Mutual Dependency
D. Transistivity
31. There are many cases when a BCNF is not used, one of them is when the relation has:
A. 2 mutually exclusive foreign keys
B. Candidate key overlap
C. 2 candidate keys and composite
D. Two or more candidate keys
32. Let us consider a small 2 way set associative cache memory which contains 4 blocks. In order to choose the block to be replaced we use the LRU (least recently used) scheme.
8, 12, 0, 12, 8
What is the total no. of cache misses for this sequence of block addresses?
A. 3
B. 2
C. 5
D. 4
33. Which of these represents an aggregate function in SQL?
A. Select
B. Distinct
C. Ordered by
D. Avg
34. Out of the options mentioned below which commands are used to control access over the objects in a relational database?
A. QUE & QUIST
B. GRANT & REVOKE
C. CASCADE & MVD
D. None
35. One particular approach of handling fuzzy logic data is designing a computer by making use of a ternary logic (base 3) such that data is stored in three forms, “TRUE”, “FALSE” and “UNKNOWN”. If each of these ternary logic elements is called a filt how many filts are necessary to represent at least 256 different values?
A. 5
B. 6
C. 7
D. 4
36. A program has two models which are executed in sequence. Let f1(t) and f2(t) provide probability density functions of the time taken to execute two possible modules. The total overall probability density function of the overall time taken to execute the program will be written as?
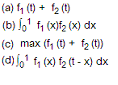
37. What can you say about a task in a blocked state?
A. It is executable
B. It is running
C. It is waiting for temporary unavailable resources
D. It must be kept in run queues
38. What is the function of semaphores?
A. They are used to do I/O functions
B. They are used for memory management
C. They synchronize critical resources in order to prevent contention
D. They synchronize critical resources in order to prevent deadlock
39. The total number of page frames which are provided to a running process in a virtual memory environment can be determined by?
A. The physical memory size
B. Page size
C. Instruction set architecture
D. Number of processes
40. In a system which involves non preemptive type scheduling there are processes which have an expected run time of 5, 18, 9, 12. What is the order in which they run so as to minimize the wait time?
A. 5, 12, 9, 18
B. 9, 12, 18, 5
C. 12, 18, 9, 5
D. 5, 9, 12, 18
Simplify the Boolean expression:
41. XY’Z’ + XY’Z’W + XZ’
42. X + X’Y’ + Y’ + (X+Y’)X’Y
43. Z(Y+Z)(X+Y+Z)
44. (X+Y)(X’+Z)(Y+Z)
45. The Boolean expression Y = (A + B + AB)C is represented by?
A. A’C
B. B’C
C. C’
D. AB
46.
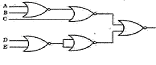
This circuilt realises what function?
A. ((A+B)’+C’)(D’E)
B. (A+B’+C)(D’E)
C. ((A+B)’+C)(D’E)
D. (A+B’+C’)(D’E)
47. Consider the circuit given in the figure:
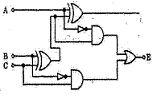
The circuit represents a:
A. Full Adder
B. Decade Counter
C. Shift Register
D. Full Subtracter
48. In order to get a correct answer when two numbers are added in excess 3 code making the sum less than 9, it is mandatory to:
A. Add 0011 to the sum
B. Add 0110 to the sum
C. Subtract 0011 from the sum
D. Subtract 0110 from the sum
49. Typical characteristic equation of an SR flip flop can be mentioned by?
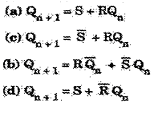
50. It is not a tree, it is a grap with n vertices and n-1 edges, what is it?
A. Connected
B. Euler
C. Circuit
D. Disconnected
51. Chromatic number of a graph if the graph requires n different colors for proper coloring?
A. K
B. K-1
C. K-2
D. K/2
52. Operations of a read bit?
A. It can be read and written by peripheral
B. It can be read and written by CPU
C. It can be read by peripheral and written by CPU
D. It can be read by CPU and written by peripheral
53. Find the eigen vectors of:
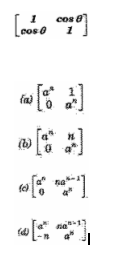
54. What does the term “aging” refer to?
A. Letting the job reside inside the memory space for a certain period of time so that the number of pages required can be estimated correctly.
B. Keeping tabs of a page which has been in the memory for LRU replacement
C. Increasing the job priority gradually so that the wait in system for a long lime is remedied.
D. Booting a process priority in multi level queue without a feedback.
55. Consider that there is a series of n tasks which come with run times r1, r2…….rn which are to be run of a uniprocessor machine. Which processor development algorithm will give rise in the throughput?
A. Shortest job first
B. First come first served
C. Highest response ratio first
D. Shortest job first
56. Consider four jobs J1, J2, J3 and J4. Here are the corresponding deadlines for the jobs:
(d1, d2, d3, d4) = (4,2,4,2)
Which statement is not a feasible option without the possibility of any deadline in the job?
A. J2, J4, J1, J3
B. J4, J2, J1, J3
C. J4, J2, J3, J1
D. J4, J1, J2, J3
57. What is the degree of resolution which can be obtained by an eight bit optical encoder?
A. 2.8 degree
B. 1.8 degree
C. 1.4 degree
D. 3.4 degree
58. What does the principle of locality of reference justify?
A. Use of interrupts
B. Use of cache memory
C. Use of main memory
D. Use of virtual memory
59. Consider this code:
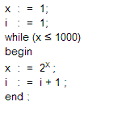
At the end of this pseudocode what is the value of i?
A. 5
B. 6
C. 7
D. 4
60. There are 5 items, 1, 2, 3, 4 and 5 which are pushed onto the stack starting from A. As such the stack is popped out 4 times and each of the elements is inserted inside a queue. 2 elements are deleted from queue and are pushed back on stack. Now, one is popped from stack. What is the popped item?
A. D
B. C
C. B
D. A
61. Round Robin scheduling can be essentially considered as the pre emptive version of?
A. FIFO
B. Longest remaining time
C. Shortest remaining time
D. Shortest job first
62. The number of 1s available in binary representation of 3 x 512 + 7 x 64 + 5 x 8 + 3 is?
A. 10
B. 12
C. 9
D. 8
63. A signal’s bandwidth is 5 kHz and its frequency at lowest level is 52 kHz, what is the highest frequency?
A. 47 kHz
B. 57 kHz
C. 10 kHz
D. 5 kHz
64. Each character code consists of 8 bits. At the baud rate of 2400 how many characters will be transmitted per second when there are 2 stop bits?
A. 216
B. 218
C. 219
D. 109
65. An Ethernet hub:
A. Operates as gateway
B. Connects to a token ring network
C. Connects to digital PBX
D. Functions as repeater
66. Where are phase transition bits used?
A. NRZ encoding
B. Manchester encoding
C. Amplitude modulation
D. Carrier modulation
67. Consider the following program:
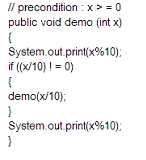
A. 3443
B. 12344321
C. 4311234
D. 1441
68. What exactly is bit stuffing?
A. Putting a 0 in user stream so that it is differentiated with a flag
B. Putting a 0 in flag stream to avoid ambiguity
C. Adding nibble to flag array
D. Adding nibble to make use of data stream
69. Name the technique in which an OS of a computer is responsible for execution of many programs simultaneously by switching to and fro in between them
A. Paging
B. Windowing
C. Multi Tasking
D. Partitioning
70. If 5 routers and 6 networks are available in an intranet making the use of link state routing, how many routing tables have been set up?
A. 1
B. 6
C. 5
D. 11
71. What is virtual memory?
A. It is a part of the main memory which has been used for swapping purposes
B. A technique which permits running of a program which is of the size more than main memory size
C. What is used in program execution
D. None
72. What is the level of aggregation of information which is needed for operational control?
A. Qualitative
B. Aggregate
C. Detailed
D. None
73. All the sets of equivalence classes of Set A and Cardinality C
A. Is of cardinality C
2B. C
2 cardinality
C. Is available with same cardinality as A
D. Forms an A partition
74. 0.75
10 = ___
8 ???
A. 0.52
B. 0.50
C. 0.54
D. 0.6
75. A ring counter is analogous to?
A. Toggle switch
B. Latch
C. SR flip flop
D. Stepping switch
76. What is the Hexadecimal equivalent to 01111100110111100011?
A. CD73E
B. F14CD
C. 7CDE3
D. ABD3F